“What? Network surveillance in my office ? Is it legal? Am I peeped at by Big Brother every day?” That’s the first outcry of an employee in one of our enterprise customers. For frequent IT security abnormal issues through network, lots of enterprises try every possible way to reduce the risk from firewall, anti-virus, content filter, anti-malware systems to integrated UTM, SIEM system. Does it work well? It depends on what kind of threats you deal with. Those threats enterprise IT security focus are most from external cyber world and could be crashed down by the above systems effectively. What about internal threats are made by disgruntled employees or malice senior management?
According to recent survey with enterprise CISO’s, more than 50% of common IT threats in enterprise, such as data leakage, sexual harassment, bullying, blackmail…etc, are from internal office environment through email, instant message, social media and internal bulletin board system. How to prevent such threats and make more comfortable and secured office environment is among top to-do list of CISO or CIO daily jobs.
On the other hand, we could also see that office automation is almost quite common in every enterprise. All business data are also shared by different teams through network inside enterprise. How to partition these data for business processes is as important as how to share these data with appropriate persons. Though lot of enterprises set up security mechanism to partition these data for business purpose, there are still a lot of holes for disgruntled or conspired employees to break in. That’s why IT governance is so important to audit all software, hardware and network systems regularly. Network surveillance is quite significant in the work of IT audit, because it can give a dynamic viewpoint and scenery of data flow inside enterprise at certain point of time or of period. This information is really helpful to recover the fact behind IT security issue.
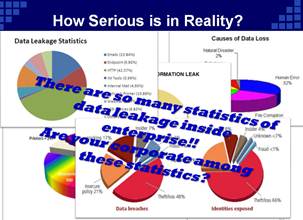 
Meanwhile, tons of data traffic inside enterprise network is seen in every office nowadays. It is almost impossible for IT security officers or auditors to check out all communication traffic of every employee. Besides, all network data are in the form of thousands of protocols. It also add some difficult to check out embedded information. That’s why network forensic equipment for network surveillance is not so popular as those systems of anti-virus, anti-intrusion inside enterprise.
“We want to provide the powerful equipment to enterprise customers in order to protect them from inside threats as well as protect employee privacy.” said Casper Chang, CEO of Decision Group. “With the functionality provided, Decision Group Enterprise Data Guard System can help to provide daily report of network activities inside office.” This report utility doesn’t only provide the facts of data leakage, IT resource abuse, unauthorized usage…etc, but it also provide report for fulfilling IT governance requirement as part of ITSM reports.
Decision Group Enterprise Data Guard System (EDGS) is the system for enterprise to deploy with internal core switch. It can collect all traffic between application servers and end users. It is capable of decoding HTTP for internal portal system, SQL transaction for data activity record, POP3, SMTP and IMAP for internal emails, access activity of MS File Server, and being Centralized Skype Monitor Center by intercepting Skype voice traffic…etc. It also provides lot of report utilities for data scoping and primary data analysis, as well as data exchange interface with 3rd party text and data mining system.
With powerful versatile functions on network traffic, EDGS will be the useful weapon in IT security management inside enterprises for both network surveillance and IT audit.
About Decision Group
Decision Group, established in 1986, is one of the leaders in manufacturing of PC-Based Multi-Port RS232/422/425 Serial Cards, Data Acquisition, Measurement Products, Industrial Automation and Control Systems. Decision Group, from the year 2000, started new line of industry involved in designing and development of equipment and software for Internet Content Surveillance and Forensics Analysis Solutions.
Decision Group also provides OEM/ODM services of its deep packet inspection (DPI) technology and solution to other partners worldwide. Decision Group has also developed a comprehensive training course, known as Network Packet Forensics Analysis Training (NPFAT), and has set up training centers worldwide for hands-on real scenario training, with certification option as well.
More Information and Contact by Email: decision@decision.com.tw
URL: www.edecision4u.com (Global), www.internet-recordor.com.tw (Taiwan), www.god-eyes.cn (China), www.decisionjapan.com (Japan) , www.decision-groups.com (Singapore), www.e-detective.de (Germany), www.edecision4u.fr (France), www.edecision4u.es (Spain and Latin America) |